What is spam, phishing and spoofing?
E-mail spoofing is often an attempt to trick the user into making a damaging statement or releasing sensitive information, such as a password. Spam and phishing emails typically use spoofing to mislead the recipient about the origin of the message.
Phishing is the attempt to obtain sensitive information such as usernames, passwords, and credit card details (and, indirectly, money). This is often for malicious reasons; by disguising as a trustworthy entity in an electronic communication. The two most common types of phishing attacks are Deceptive Phishing and Spear Phishing:
- Deceptive Phishing is the most common type of phishing scam. It refers to any attack by which fraudsters impersonate a legitimate company and attempt to steal people’s personal information or login credentials. Those emails frequently use threats and a sense of urgency to scare users into doing the attackers’ bidding. The success of a deceptive phish hinges on how closely the attack email resembles a legitimate company’s official correspondence. As a result, users should inspect all URLs carefully to see if they redirect to an unknown website. They should also look out for generic salutations, grammar mistakes, and spelling errors scattered throughout the email.
- Spear Phishing is much cleverer as it uses a high degree of personalisation. For instance, in spear phishing scams, fraudsters customise their attack emails with the target’s name, position, company, work phone number and other information. This is done in an attempt to trick the recipient into believing that they have a connection with the sender. The goal is the same as deceptive phishing: lure the victim into clicking on a malicious URL or email attachment, so that they will hand over their personal data.
How to spot malicious emails
Keep Informed About Phishing Techniques
New phishing scams are being developed all the time. Without staying on top of these new phishing techniques, you could inadvertently fall prey to one. Keep your eyes peeled for news about new phishing scams. By finding out about them as early as possible, you will be at much lower risk of getting snared by one.
Think Before You Click!
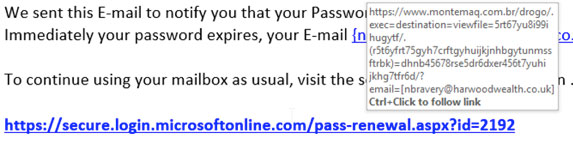
Phishing emails, purporting to be from a genuine person whose name you recognise, will often contain a mismatched URL. If you are suspicious, hover your mouse over the top of the URL and you should see the actual hyperlinked address. If the hyperlinked address is different from the address that is displayed, the message is probably fraudulent or malicious.
Example: The link shows https://secure.login.microsoft.com… however if you hover over the link, the URL is shown www.montemaq…
People who launch phishing scams often depend on their victims not knowing how the DNS naming structure for domains works. The last part of a domain name is the most important piece of information to check:
Example: info.brienposey.com would be a child domain of brienposey.com because brienposey.com appears at the end of the full domain name (on the right-hand side).
Conversely, brienposey.com.maliciousdomain.com would clearly not have originated from brienposey.com because the reference to brienposey.com is on the left side of the domain name.
Phishing scams try to convince victims that a message comes from a company like Microsoft or Apple. The scammer simply creates a child domain bearing the name Microsoft or Apple, for example. The resulting domain name looks something like this: Microsoft.maliciousdomainname.com
When in doubt, go directly to the source rather than clicking a potentially dangerous link. Do NOT open suspicious emails from addresses that you don’t recognise, or emails purporting to be from inside your organisation that you were not expecting. Mark them as Junk within Outlook or delete them immediately. Remember a genuine organisation will try to contact you again if their email is urgent.
Verify a Site’s Security
It’s natural to be a little wary about supplying sensitive financial information online. As long as you are on a secure website, however, you shouldn’t run into any trouble. Before submitting any information, make sure the site’s URL begins with “https” (the inclusion of the s is important). There should also be a “closed lock” icon near the address bar. Check for the site’s security certificate as well.
If you get a message stating a certain website may contain malicious files, do not open the website. Never download files from suspicious emails or websites. Even search engines may show certain links which may lead users to a phishing webpage which offers low cost products. If a user makes purchases at such a website, the credit card details will be accessed by cybercriminals.
Check Your Online Accounts Regularly
If you don’t visit an online account for a while, someone could be having a field day with it. Even if you don’t technically need to, check in with each of your online accounts on a regular basis. Get into the habit of changing your passwords regularly too. To prevent bank phishing and credit card phishing scams, you should personally check your statements regularly. Get monthly statements for your financial accounts and check each and every entry carefully to ensure no fraudulent transactions have been made without your knowledge.
Keep Your Browser Up to Date
Security patches are released for popular browsers all the time. They are released in response to the security loopholes that phishers and other hackers inevitably discover and exploit. If you typically ignore messages about updating your browsers, stop. The minute an update is available, download and install it.
Be Wary of Pop-Ups
Pop-up windows often masquerade as legitimate components of a website. All too often, though, they are phishing attempts. Many popular browsers allow you to block pop-ups; you can allow them on a case-by-case basis. If one manages to slip through the cracks, don’t click on the “cancel” button; such buttons often lead to phishing sites. Instead, click the small “x” in the upper corner of the window.
Never Give Out Personal Information
As a general rule, you should never share personal or financially sensitive information over the Internet. When in doubt, visit the main website of the company in question, get their number and give them a call. Most phishing emails will direct you to pages where entries for financial or personal information are required. An Internet user should never make confidential entries through the links provided in the emails. Never send an email with sensitive information to anyone. Make it a habit to check the address of the website. A secure website always starts with “https”.
It’s too Good to be True
If you receive an email message informing you “…you’ve won the lottery…” or “…congratulations you are the winner…” – however you have not bought a lottery ticket or entered a competition, it’s likely to be a malicious email. If something seems too good to be true, it probably is. If you receive a message from someone unknown to you, making big promises, the message is probably a scam.
You’re Asked to Send Money
One sign of a phishing email is that you will eventually be asked for money. You might not be asked in the initial message, but sooner or later, phishing criminals will likely ask for money. They will claim it is to cover expenses, taxes, fees, or something similar.
These emails can appear to come from your Managing Director or someone very senior in your organisation, and will often carry a sense of urgency. Never respond to such emails. If you think it really is genuine, double check by phoning the sender; do not reply to the email itself.
You Receive Threats and there is a Sense of Urgency
Most phishing scams try to trick people into giving up sensitive information or cash by promising instant riches. However, some phishing criminals use intimidation to scare victims into giving up information. If a message makes unrealistic threats, it is probably a scam.
Example: You receive a letter stating “your account has been compromised and if you do not submit a form (which asks for your account number, along with two signature samples) your account will be cancelled and your assets will be seized”.
If you get an email telling you that if you act now you will get 50% discount or a free gift, be wary. One of the ways cyber criminals achieve success is by offering you incentives to act in a tight timeframe.
Poor Spelling and Grammar
When a large company sends out a message on behalf of the company as a whole, the message is usually reviewed for spelling and grammatical errors. If a message is filled with poor grammar or spelling mistakes, it probably didn’t come from the genuine major corporation.
Protecting your data from cybercrime
The weakest link in any business is its people. Unfortunately, we can all fall victim to cybercrime. Phishing attempts are becoming ever more sophisticated and we must be ever more vigilant. There are things you can do to protect your data, as follows:
- Implement our customisable IT Acceptable Usage Policy
- Share this Guide with your staff
- Implement a Password Policy
- Implement a Document Encryption Guide
- Use Antivirus Software and regularly back up your data
We can help!
For further advice or to talk to an IT professional, please email [email protected] or call 02392 007850.